Stackoverflowoops There Has Been an Error Please Try Again Later
- Details
- Reviews
- Installation
- Back up
- Evolution
Secure WordPress login with this 2 factor authentication (TFA / 2FA) plugin. Users for whom information technology is enabled volition crave a one-fourth dimension lawmaking in social guild to log in. From the authors of UpdraftPlus – WP'southward #one fill-in/restore plugin, with over two one thousand thousand active installs.
Are y'all completely new to TFA? If so, please run into our FAQ.
Features (please see the "Screenshots" for more data):
- Supports standard TOTP + HOTP protocols (and and so supports Google Authenticator, Authy, and many others).
- Displays graphical QR codes for easy scanning into apps on your telephone/tablet
- TFA tin exist fabricated bachelor on a per-office basis (e.g. bachelor for admins, but not for subscribers)
- TFA tin can be turned on or off by each user
- TFA can exist required for specified user levels, later on a divers fourth dimension menstruation (eastward.thousand. require all admins to have TFA, once their accounts are a calendar week erstwhile) (Premium version), including forcing them to immediately prepare up (by redirecting them to the folio to practise and so)
- Supports front end finish-terminate editing of settings, via [twofactor_user_settings] shortcode (i.e. users don't need admission to the WP dashboard). (The Premium version allows custom designing of any layout y'all wish).
- Site owners can let "trusted devices" on which TFA codes are but asked for a called number of days (instead of every login); e.k. 30 days (Premium version)
- Works together with "Theme My Login" (both forms and widgets)
- Includes back up for the WooCommerce and Affiliates-WP login forms
- Includes support for Elementor Pro login forms (Premium version)
- Includes support for bbPress login forms (Premium version)
- Includes support for whatever and every 3rd-party login form (Premium version) without any farther coding needed via appending your TFA lawmaking to the end of your password
- Does non mention or request second factor until the user has been identified as i with TFA enabled (i.e. nix is shown to users who do not have it enabled)
- WP Multisite compatible (plugin should be network activated)
- Simplified user interface and code base for ease of utilize and performance
- Added a number of actress security checks to the original forked code
- Emergency codes for when you lose your phone/tablet (Premium version)
- When using the front-stop shortcode (Premium version), require the user to enter the current TFA code correctly to be able to activate TFA
- Works together with "WP Members" (shortcode form)
- Administrators tin can access other users' codes, and turn them on/off when needed (Premium version)
Why employ TFA / 2FA ?
Read this! https://www.wired.com/2012/08/apple-amazon-mat-honan-hacking/
How Does TFA / 2FA Work?
This plugin uses the industry standard TFA / 2FA algorithm TOTP or HOTP for creating 1 Time Passwords. These are used by Google Authenticator, Authy, and many other OTP applications that you can deploy on your phone etc.
A TOTP code is valid for a sure fourth dimension. Whatever plan y'all utilize (i.e. Google Authenticator, etc.) volition prove a different code every so frequently.
Plugin Notes
This plugin began life in early on 2022 equally a friendly fork and enhancement of Oscar Hane'southward "two cistron auth" plugin.
-
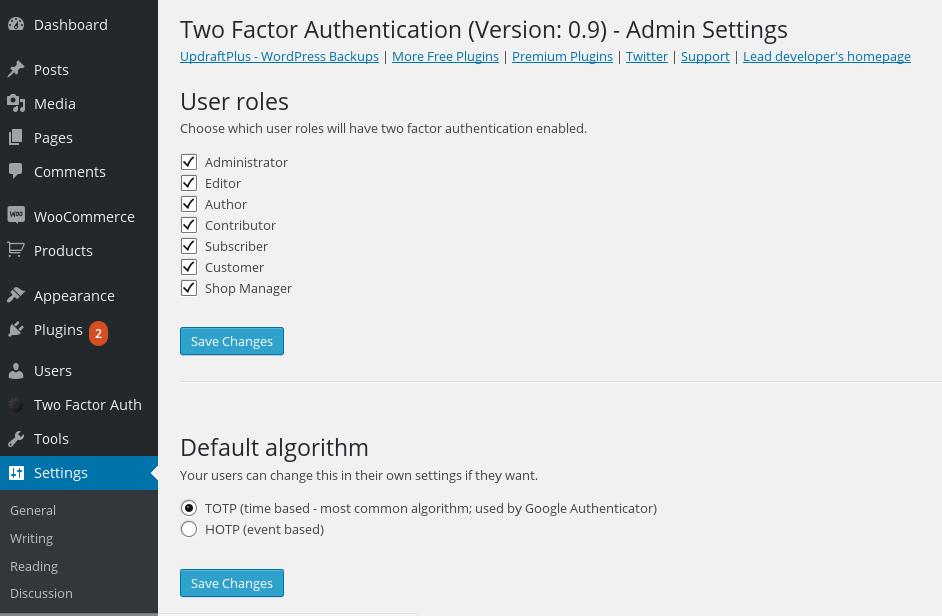
Site-wide settings
-

User settings (dashboard)
-

User settings (front end-end, via shortcode)
-
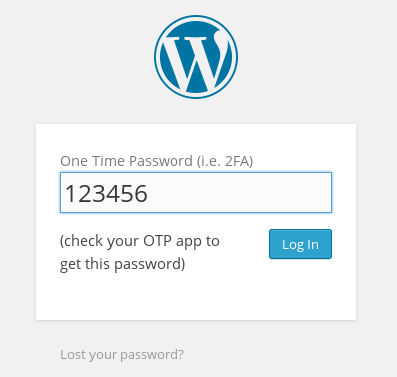
Regular WP login course requesting OTP code (after successful username/password entry)
-
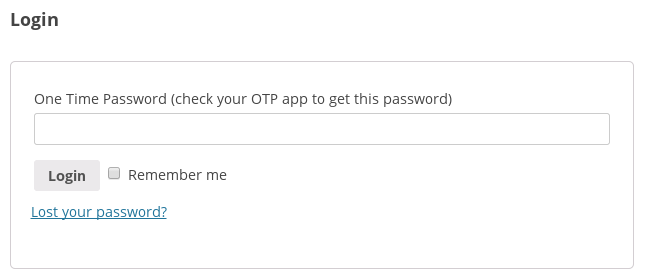
WooCommerce login grade requesting OTP code (afterward successful username/countersign entry)
-

What the user sees if opening a incorrect OTP code on the regular WP login course
-

What the user sees if opening a incorrect OTP code on the WooCommerce login form
-
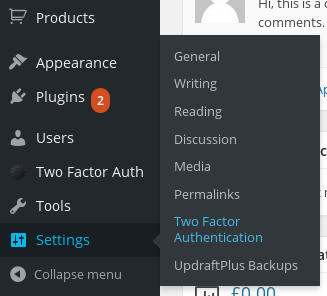
Where to observe the site-broad settings in the dashboard menu
-
Where to find the user's personal settings in the dashboard menu
-
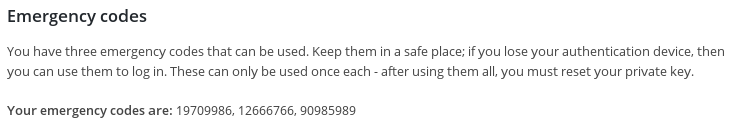
Emergency codes (Premium version)
-
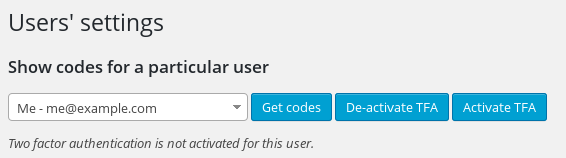
Adjusting other users' settings as an admin (Premium version)
-

Edifice your ain design for the page with custom curt-codes (Premium version)
This plugin requires PHP version 5.3 or higher and back up for either php-openssl or PHP mcrypt. The vast majority of PHP setups will have one of these. If not, inquire your hosting visitor.
- Search for 'Two Cistron Authentication' in the 'Plugins' carte du jour in WordPress.
- Click the 'Install' button. (Brand certain yous picks the right i)
- Activate the plugin through the 'Plugins' carte du jour in WordPress
- Find site-wide settings in Settings -> 2 Factor Authentication ; detect your own user settings in the top-level neb of fare entry "Two Factor Auth".
If you want to add together a section to the front end-finish of your site where users tin configure their 2-gene authentication settings, utilize this shortcode: [twofactor_user_settings]
-
What is two gene authentication (TFA / 2FA) ?
-
Basically, information technology's to practice with securing your logins, so that in that location's more i link in the concatenation needing to be broken before an unwanted intruder tin can go in your website.
By default, your WordPress accounts are protected by merely one thing: your password. If that'south broken, then everything'south broad open up.
"Two factor" means adding a 2d requirement. Usually, this is a code that comes to a device y'all ain (due east.g. telephone, tablet) – so, someone can't get into your website without getting concur of your device. Yous tin tin become a longer answer from Wikipedia.
Sometimes information technology is also called multi-factor hallmark instead of two-factor – considering someone could secure their systems with equally many factors as they like.
-
Why should I intendance?
-
Read this: https://www.wired.com/2012/08/apple-amazon-mat-honan-hacking/
-
How does ii factor authentication (TFA / 2FA) work?
-
Since "ii gene hallmark" only means "a second something is necessary to go far", this reply depends upon the detail gear up-upward. In the most common case, a numeric code is shown on your phone, tablet or other device. This lawmaking be sent via an SMS; this so depends on the mobile phone network working. This plugin does not uses that method. Instead, it uses a standard mathematical algorithm to generate codes that are simply valid once each, or for simply for 30 seconds (depending on which algorithm you cull). Your phone or tablet tin know the code afterward information technology has been fix up once (often, past just scanning a bar-lawmaking off the screen).
-
What exercise I demand to set up on my telephone/tablet (etc.) in social club to generate the codes?
-
This depends on your particular brand of telephone, and your preferences. Google have produced a popular app chosen "Google Authenticator", which is a preferred option for many people because information technology is easy to apply and tin can be ready up via merely scanning a bar code off your screen – follow this link, and ignore the outset paragraph that is talking almost 2FA on your Google business relationship (rather than beingness relevant to this plugin).
-
What if I do not accept a phone or tablet?
-
Many and diverse devices and programs tin generate the codes. one pick is an add-on for your web browser; for example, here are some apps and add together-ons for Google Chrome. Wikipedia lists diverse programs for dissimilar computers.
-
I lost my device that has laissez passer-codes – or, they don't piece of work. What to practice?
-
If your laissez passer-code used to work, but no longer does, so bank bank check that the time on your device that generates them is authentic.
If y'all cannot go in and need to disable two-gene authentication, and and then add together this to your wp-config.php file, using FTP or the file managing director in your hosting command console:
define('TWO_FACTOR_DISABLE', truthful);Add information technology adjacent to where whatever other line showtime with "ascertain" is.
Alternatively, if y'all accept FTP or cPanel admission to your web hosting space, you lot tin de-activate the plugin; see this article.
-
Why does the plugin non support sending the two-gene code by e-mail service?
-
If someone has access to your email account, and so they can send a password-reset lawmaking there using the password-reset mechanisms congenital into WordPress. Therefore, if the ii-gene lawmaking was as well sent in that location, then power to read your electronic mail allows the breaking of both factors, and hence is no longer truly two cistron authentication.
Some users might have 2 cistron hallmark on their email account, simply this is not knowable or controllable from within WordPress, and and and so giving this pick to users ways that the ambassador cannot encounter or enforce two-factor hallmark. And fifty-fifty in this case, e-mail is often sent between servers unencrypted, and and so is susceptible to human being-in-the-middle attacks across the control of WordPress.
-
What are HOTP and TOTP?
-
These are the names of the two mathematical algorithms that are used to create the special codes. These are industry-standard algorithms, devised by expert cryptographers. HOTP is less popular, but the device that generates the codes does non need to know the correct time (instead, the codes are generated in a precise sequence). TOTP is much more pop, and generates codes that are but valid for 30 seconds (and so your device needs to know the time). I'd recommend TOTP, as HOTP tin can be annoying if something causes the sequences to leave of sync.
-
What is the shortcode to utilise for front-end settings?
-
[twofactor_user_settings]
-
I deliberately entered a wrong countersign, and it let me login!
-
You have a password manager extension installed in your spider web browser, with the correct password entered in it. Information technology has automatically replaced your wrong password with the right i from its saved shop. This behaviour has been observed and confirmed by several users. You can verify information technology by using the spider web developer tools in your browser to look at the HTTP information sent to WordPress, and notice which password is really in it. Y'all tin also open up a fresh web browser with no such extension in data technology to re-test.
Note that the two cistron authentication plugin has no mechanism to compare or corroborate passwords; this is washed past WordPress cadre. If the wrong password is sent, and and so this is handled by WordPress, and the login volition not go on.
Payed only? Not ready for PHP-8 ? Asking for server features non being available?
Does the job without any troubles. Works with Google Authenticator and the Microsoft Authenticator as well. I besides recommend the plugins large brother: "UpdraftPlus - Rubber & restore"
I have used this production on a dozen of the websites I have congenital and take had positive results without exception. The plugin is maintained regularly and works with a diversity of Authenticator apps. Neat product, Highly recommended!
In the trial version I tried to brand a specific user role to be requested (not forced) to setup his authenticator APP (i.eastward. FreeOTP), just information technology did non piece of work at all as the plugin did non exist at all. At least it did non do any impairment. Information technology was a compassion since this plugin was promising. UPDATE: After activating the plugin and put the shortcode [twofactor_user_settings] in the front end of the website (in an Elementor cake), after a while a long text appeared in the front-cease where it should accept been, but it did not recognize a the password of test-user I was testing. Overall, information technology seems to me also difficult to make it working, and information technology is a pity since this plugin apperared to exist promising as others as well. I gave up. And and then far, I got something working only from "miniorange ii factor hallmark". Sometimes, while testing dissimilar plugins of this kind, I even concluded locked out my website with no take a chance to log in once again. Luckly I was doing all testing on a staging website and I do recommend doing the same with these dangerous plugins (they either practise not piece of work at all – every bit this i – or lock y'all out). For the paid version of this type of plugin, I also do recommend to get a full effort-earlier-buy testing, otherwise practice forget well-nigh them.
First footstep goes already wrong. Google Authenticator says "Invalid Barcode" when trying to enable the 2FA.
Install, activate and setup all were similar shooting fish in a barrel. We used Google Authenticator and this works well. The number of failed hacker login attempts has decreased dramatically.
Read all 70 reviews
"Two Gene Authentication" is open source software. The post-obit people have contributed to this plugin.
Contributors
i.14.three – 26/Jan/2022
- TWEAK: Change internal translation building and loading mechanism
- TWEAK: "https://" is not a translatable cord
- TWEAK: Load translations even if aborting due to incompatible PHP version
- TWEAK: Update updater libraries to electric current versions
one.14.i – 08/Nov/2021
- REFACTOR: The constants SIMBA_TFA_PLUGIN_DIR and SIMBA_TFA_PLUGIN_URL have been abolished. If y'all had manus-coded whatsoever lawmaking that used them, then yous will desire to review and test your customisations advisedly showtime. This applies for all refactoring items and internal changes mentioned below.
- REFACTOR: Internal plugin directory construction changed
- TWEAK: Fix a potential PHP coding notice in 1.13.0 when an administrator viewed a user's QR lawmaking
i.13.0 – 01/November/2021
- REFACTOR: Consummate re-organization of all Premium lawmaking. If you lot had paw-coded whatsoever code which interacted with information technology, yous will want to review and exam your customisations carefully first. This applies for all refactoring items and internal changes mentioned beneath.
- REFACTOR: Abolished the form Simba_TFA_Plugin_Admin_Dashboard_Integration
- REFACTOR: Moved some TOTP/HOTP-specific methods out of Simba_Two_Factor_Authentication into Simba_TFA_Provider_TOTP
- TWEAK: Class TFA_Frontend renamed to Simba_TFA_Frontend
- TWEAK: The constant SIMBA_TFA_PLUGIN_FILE is no longer used internally and has been abolished
- TWEAK: Move Premium plugin update loader into the main Premium class
- TWEAK: Gene out all Premium features into individual classes
- TWEAK: The method tfa_is_available_and_active() has been removed.
- TWEAK: The method Simba_TFA_Provider_TOTP::getPanicCodesString() has been renamed to Simba_TFA_Provider_TOTP::get_emergency_codes_as_string()
1.12.three – 22/October/2021
- Set: Fix the twofactor_user_qrcode shortcode in the Premium version
one.12.two – 21/Oct/2021
- Gear up: Forestall load-order related fatal error (regression since ane.12.0) on sites that did not have AUTH_KEY divers in wp-config.php
- TWEAK: Update updater library in Premium version to latest version
- TWEAK: Introduce templating method for better code system
1.12.1 – 18/Oct/2021
- REFACTOR: Continuing the major re-factor of the plugin's internal classes. If you had mitt-written custom PHP lawmaking that hooks into whatsoever internal classes, you volition want to review your customisations carefully starting time.
- TWEAK: Update .pot file
ane.12.0 – xvi/Oct/2021
- REFACTOR: Major re-factor of the plugin'due south internal classes. If y'all had hand-written custom PHP code that hooks into whatever internal classes, you lot will want to review your customisations carefully start.
- TWEAK: Harmonise wording on trusted devices label
- TWEAK: Remove redundant hex2bin compatibility for no-longer-supported PHP versions
ane.eleven.0 – 14/Sep/2021
- Characteristic: (Premium) Add new anti-bot feature for WooCommerce login forms: practice not include the login class within the folio HTML (making them invisible to almost bots), bringing it dorsum via JavaScript. The feature needs to exist activated witin the plugin settings.
1.x.4 – 27/Jul/2021
- TWEAK: Fix a couple of minor visual regressions in the WooCommerce login course TFA field layout
one.x.3 – 28/Jun/2021
- FIX: Incorrect object reference in Affiliate WP integration (regression in i.10.0)
i.ten.ii – 26/Jun/2021
- TWEAK: The script tfa_frontend.php at present uses an external JavaScript file (better compatibility with with content security policies)
ane.10.i – 25/Jun/2021
- Prepare: Gear up a bug in the Premium Elementor integration introduced in 1.x.0.
ane.ten.0 – 15/Jun/2021
- REFACTOR: Integrate the previously-divide WooCommerce/Affiliates-WP handlers in the main handler, eliminating redundant/duplicate code. Eliminate the internal concept of dissimilar form types by re-coding the few "type one"s as type twos. Divide login-course specific information from code.
one.nine.6 – 04/Jun/2021
- Feature: Back up bbPress login forms (Premium version)
1.9.5 – 26/May/2021
- TRANSLATIONS: Update bundled Castilian translation (es_ES) in Premium release
one.9.4 – 25/May/2021
- Gear up: Preclude an issue identifying the username field when on a page with both Affiliates WP login and registration forms, when the login form displayed second
i.9.3 – 14/April/2021
- Ready: In the Premium version, when appending the TFA code to the countersign on third-party login forms with no directly back up, just usernames were accustomed for the login (not electronic mail addresses)
one.9.two – 20/Mar/2021
- TWEAK: When checking if a user has TFA enabled on a login page, perform the aforementioned sanitisation on the username as WP core, and then that if the user mis-types their username (which WP accepts) e.g. past prefixing a infinite, then they will nonetheless be asked for their TFA lawmaking (instead of jumping directly to an error for not supplying one)
- TRANSLATIONS: Added an Italian translation, thank you to Edoardo Di Leginio
one.9.ane – 15/February/2021
- TWEAK: Correct the "for" aspect of the "marking as trusted" text label on the WooCommerce login form
i.9.0 – 09/February/2021
- FEATURE: (Premium) If TFA is required for a user, and they have non still set up it upwards, then force them to be redirected to a configured URL
- TWEAK: Supervene upon the deprecated jQuery.click() and .modify() methods
1.viii.8 – sixteen/Jan/2021
- TWEAK: Supercede the deprecated jQuery.unbind() and .focus() methods
- TWEAK: If the free version is active, then throw an mistake if trying to actuate the Premium version, explaining what needs to be done
1.8.vii – 11/Jan/2021
- TWEAK: Update jQuery certificate prepare, click and submit styles to one not deprecated in jQuery 3.0, and supervene upon :showtime pseudo-selector with .commencement()
- TWEAK: At present marked as supporting PHP 5.vi+ (now that PHP 8.0 is out)
- TWEAK: Update to the latest version of the arranged updater library (paid versions), which adds integration with WP 5.five+'southward motorcar-updater
i.8.six – 15/Sep/2020
- FEATURE: Add a 'TFA' column also to the Users screen in the WP network admin dashboard (multisite installs)
- TWEAK: Update the arranged updater library (paid versions) to the current release
1.viii.5 – 29/Aug/2020
- TWEAK: Fix the "for" attribute of the "trusted" text label on the WooCommerce login form
- TWEAK: If a website's wp-login.php is available under multiple hosts without CORS enabled betwixt them, and so AJAX calls would fail; this is now resolved by using a relative URL instead
- TWEAK: Update bundled updater libraries on Premium version (improving compatibility with WP v.5+'s update settings)
one.8.four – 26/May/2020
- TWEAK: Updare .pot file; now both the offset 2 parameters to _n() are too included in the aggregation procedure
1.8.2 – 23/May/2020
- Fix: If the site possessor was requiring a correct code to be supplied for activation, and then this was too existence required for de-activation
- TWEAK: Introduce simbatfa_enforce_require_after_check filter, allowing developers to selectively disable the "require TFA later 10 days" depository financial institution check
- TWEAK: Update .pot file
1.viii.0 – 18/April/2020
- Feature: Add support in the paid version for Elementor login forms
- TWEAK: Updater in paid version now will brand checks on availability without needing login
- TWEAK: Update updater class to electric electric current release
1.seven.iv – xix/Mar/2020
- TWEAK: Adjust how the trusted field is referenced from JavaScript, fixing IE11 compatibility
- TWEAK: Introduce the filter simba_tfa_required_for_user
1.vii.iii – 03/Mar/2020
- TWEAK: Provide not-plural culling for trusted device phrase
- TWEAK: Marking equally supporting WP five.4
1.7.2 – 13/Feb/2020
- TWEAK: Update message nigh what to exercise with translations
ane.vii.ane – xiv/January/2020
- Fix: Missing file in i.vii.0 (free) release
ane.7.0 – xiv/January/2020
- Feature: (Premium version): Add an optional TFA section to the WooCommerce business relationship details section in "My Business relationship"
- TWEAK: Fix div tag balancing issue in settings output
- TWEAK: Update WooCommerce integration to arrange to DOM changes in WooCommerce iii.viii
- TWEAK: Update .pot file
1.half-dozen.4 – 12/Nov/2019
- TWEAK: On wp-login.php on WordPress 5.3, the password field was not hiding when the TFA field opened
- TWEAK: Update .pot file
- TWEAK: Add data-lpignore attribute to TFA field to signal to LastPass that it is not a countersign field
one.6.3 – eighteen/October/2019
- Fix: The 'trusted users' selection display in the settings defaulted to showing as enabled, whereas in fact the default setting is disabled
- TWEAK: Mark equally compatible with WP 5.three
1.six.2 – xi/Sep/2019
- Gear up: On multisites, assistants of site users who were not nowadays on the primary site was not possible
- TWEAK: Introduce the WP action simba_tfa_activation_status_saved to allow developers to answer to activation condition changes
- TWEAK: Update updater class to 1.eight series
i.half dozen.i – ten/Aug/2019
- TWEAK: Response to an endeavor to plow TFA on can at present include an "error" aspect if the attempt failed due to failure to supply the electrical current code
1.6.0 – 08/Aug/2019
- Characteristic: (Premium version) Past using the parameter fashion="require_current" with the shortcode twofactor_user_settings_enabled, the user will just be able to actuate TFA if they enter the current TFA code
- TWEAK: Remove the incorrect suffix "(Premium)" (double-suffix in the actual Premium version) that appeared in the plugin championship in ane.5.half dozen
i.5.6 – 06/Aug/2019
- TWEAK: Permit customisation of a item message via a filter simbatfa_message_you_should_verify
- TWEAK: Supervene upon "eachother" with "each other"
1.5.five – 30/Jul/2019
- TWEAK: Strength a global context when creating the initial Simba_Two_Factor_Authentication object, to piece of work around direct accesses from components that exercise not prepare the scope correctly
1.five.4 – 17/Jul/2019
- Feature: (Premium version) – allow the site ambassador to forbid users who accept compulsory TFA to turn information technology off (supplementing the boosted adequacy to prevent them logging in)
1.five.3 – 22/Jun/2019
- TWEAK: When using your last emergency lawmaking (Premium version), and viewing your settings (which regenerated new ones), then if yous did not follow the communication to reset your prviate key, y'all would get the same codes as before. This might exist idea undesirable (though is not a security flaw, as the emergency codes are no more guessable the 2nd fourth dimension effectually than the beginning). This behaviour has at present been inverse.
i.v.ii – 08/Jun/2019
- TWEAK: When php-mcrypt was not installed, pressing the "Reset private central" link in a user'south settings would cause an unnecessary PHP observe, and brandish a incorrect "current code" for a few seconds.
ane.five.1 – 05/May/2019
- Characteristic: Back up any login form (Premium version) via appending the TFA lawmaking onto the finish of the countersign. This allows support fifty-fifty of login forms coded in a way that make integrations (that aren't hacks or inordinate amounts of piece of work-effectually lawmaking) impossible (e.chiliad. PeepSo)
- TWEAK: Minor wording tweak in the explanation of how TOTP works.
i.iv.12 – eighteen/April/2019
- TWEAK: Add together a filter simba_tfa_localisation_strings assuasive further customisation of forepart-stop strings
- TWEAK: Add an extra instructional message in the "Make 2 cistron authentication compulsory" section (Premium) to explicate how to cope with existing users
- TWEAK: Cope with the user entering spaces in their two-gene code (TOTP protocol codes are numbers just, but some apps patently brandish formatting and users are non aware)
- TWEAK: Mark as supporting WP five.2
ane.four.eleven – 08/Mar/2019
- FIX: On multisites, the user search should search on all sites, non just the principal one
ane.4.10 – 01/Mar/2019
- TWEAK: Introduce a filter, simba_tfa_management_capability, assuasive the WP capability (default: manage_options) required by a user to manage the plugin to exist inverse. (Be conscientious – giving the ability to manage could potentially mean the ability to lock whatever user out).
1.4.9 – 20/February/2019
- SECURITY: The security fix in version 1.four.vii was faulty and failed to completely set up the problem; it is at present resolved in this release. Our apologies for the double update.
one.four.8 – xvi/Feb/2019
- FIX: On some multisite setups, the link to the site-wide assistants settings went to the wrong identify
ane.4.vii – 06/Feb/2019
- SECURITY: If a user's WordPress account username was in the course of an email accost, and if their actual business human relationship e-mail accost was something different, and TFA was set upwardly on that account, and used the "username" (that looked similar an email address) to login, then TFA controls upon login on that account would be ineffective. Other accounts were not afflicted (regardless of whether you login by e-mail or not). This vulnerability was inherited from the original "2 Factor Auth" plugin that this plugin was forked from, and then is present in all versions before this i.
1.iv.6 – 05/Feb/2019
- Gear up: When displaying a user's trusted devices in the admin folio, the time that a device was trusted until was not shown correctly (instead, it showed the current time)
- Gear upwardly: Removing the offset trusted device in a list did not eastward'er work
- TWEAK: Brandish "(none)" when in that location are no trusted devices
ane.4.4 – 04/Feb/2019
- Characteristic: Trusted devices are now listed in the user's admin folio, assuasive them to come across and remove trust from their devices.
- TWEAK: Updated .pot file
i.four.iii – 28/Jan/2019
- Prepare: The "Trusted devices" functionality (Premium) checkbox was not actualization when activated
- TWEAK: Add together a missing translation domain to a phrase
ane.four.ane – 25/January/2019
- FEATURE: Trusted devices: A site possessor can now choose to let particular user levels (due east.one thousand. admins, editors) to mark devices as 'trusted' and thereby exempt from needing to enter a TFA lawmaking for a called number of days. This feature is off past default and requires https (i.e. SSL) on the login grade and cookies to be kept in the trusted device.
- FIX: Set a regression in 1.four.0 whereby when a site owner viewed some other user'due due south electric current lawmaking, information technology could subsequently cocky-update with the incorrect user'south value
- TWEAK: Add the robustness in parsing broken JSON present on the standard WP login form to other login forms
- TWEAK: Diverse internal code documentation improvements
- TWEAK: Suppress mcrypt deprecation notices in places where we would use an alternative if information technology was non present
- TWEAK: Bumped the back upwards requirement up to WP three.4. I'm not enlightened of anything done to intermission information technology on three.iii, only this is the official requirement (it's very difficult to exam sometime WP versions as they don't run on modern webserver stacks)
i.four.0 – 24/January/2019
- Characteristic: Where the electric current OTP lawmaking is displayed (during setup), this will at present self-update automatically (i.e. without needing a transmission press on the "update" link).
- TWEAK: Various improvements to the layout and text of the setup page to assist make the process more than understandable
- TWEAK: The current code is shown next to the UI pick for enabling TFA
- TWEAK: Prevent a PHP notice if AUTH_KEY was not defined (on some very quondam WP installs)
i.three.xiii – 18/Dec/2018
- SECURITY: Ready a logged-in CSRF vulnerability reported by Martijn Korse (www.bitnesswise.com). Due to a missing nonce bank check, if an assaulter was able to persuade a personally-targetted victim who was currently logged in to their WordPress concern relationship to visit a personally-crafted (for the individual victim) folio in the same browser session, and so the attacker would exist able to de-activate 2-factor hallmark for the victim on that WordPress site (thus leaving the targetted business relationship protected by the user's countersign, simply non by a second factor – the absence of a request for a TFA code would be credible on the user'southward next login). This vulnerability was inherited from the original "Two Gene Auth" plugin that this plugin was forked from, and and then is present in all versions earlier this one.
- TWEAK: Some minor code-tidying
- TWEAK: Update bundled Premium updater library to current version (1.five.ten)
one.three.12 – 14/Dec/2018
- TWEAK: Forbid a PHP debugging discover when $pagenow is not set
i.iii.11 – 04/December/2018
- Feature: Add together a 'TFA' column on the Users screen in the WP admin dashboard to brandish TFA status, cheers to Enrico Sorcinelli.
i.iii.10 – thirty/Nov/2018
- FIX: TFA codes were not beingness requested on the login course on a WooCommerce dedicated social club payment page (i.eastward. /checkout/gild-pay/123456/?pay_for_order=truthful&fundamental=wc_order_blahblahblah) (pregnant that if a user had TFA activated, login would fail).
- TWEAK: Forbid a PHP find if AUTH_SALT was non defined (on some very old WP installs)
i.3.9 – 30/Oct/2018
- SECURITY: If you were non using the recommended selection of requiring 2FA for XMLRPC requests, and then an attacker could potentially too featherbed requirements for 2FA on ordinary logins (i.east. only need the countersign). Such users will want to immediately update, though we recommend that all users practice. This vulnerability was inherited from the original "Two Gene Auth" plugin that this plugin was forked from, and and so is nowadays in all versions before this 1.
i.3.viii – 25/October/2018
- TWEAK: Update the updater class in the Premium version to the electric current release (i.5.vi)
1.iii.7 – 15/October/2018
- TWEAK: Endeavor to mitigate plugins on the login page which cause JavaScript exceptions by enqueing our scripts earlier.
1.three.half-dozen – 04/Oct/2018
- TWEAK: Add aspect autocomplete="off" on the WooCommerce login class TFA field (was already present for regular WP login form)
- TRANSLATION: Added Portuguese (Brazilian) translation, courtesy of Dino Marchiori
one.3.v – 02/October/2018
- TWEAK: Some code-styling consistency clean-ups
- TWEAK: Allow one more than window'south tolerance by default for codes from devices running fast
1.three.4 – xi/Sep/2018
- FIX: Sometimes a TML widget login form could fail to work because of a inverse/unexpected DOM tree
- Gear up: Some further breakage in TML had occurred, causing login buttons to require to exist pressed twice
1.iii.3 – 31/Jul/2018
- FIX: Restore support for "Theme My Login", which had been cleaved by unannounced changes in TML 7.x
- TRANSLATIONS: Update .pot file
1.3.two – 31/May/2018
- TWEAK: Add the simbatfa_check_tfa_requirements_ajax_response and simbatfa_verify_code_and_user_result filters to let over-riding of the response to the "TFA required?" question and the TFA depository financial institution check itself by developers
ane.3.1 – 25/May/2018
- Set up: The WooCommerce three.iii+ login form was requiring 2 clicks on the 'Log In' push
- TWEAK: The progress spinner had disappeared on WooCommerce three.3+
i.3.0 – 05/April/2018
- FEATURE: (Premium version) Integration with the WP-Members login form, https://wordpress.org/plugins/wp-members/ . N.B. WP-Members does not laissez passer on the existent error bulletin upon a login failure, but displays its ain hard-coded message that the username/password were wrong; and then you'll see this even if information technology was actually the TFA code that was incorrect.
- TWEAK: Change the permission cheque for editing other users (Premium version) to edit_users (instead of the previous update_plugins, intended simply as a proxy for "is an admin")
- TWEAK: End using the deprecated jQuery.parseJSON method
- TWEAK: Change a cord that was non in a translatable class
- TWEAK: Update the updater class in the Premium version to the current release (1.5.1)
1.2.35 – 28/November/2017
- TWEAK: Upon front end-end settings salvage, do jQuery(certificate).trigger('tfa_settings_saved'), allowing the user to reply to the action (e.g. reload page)
- TWEAK: Suppress mcrypt deprecation notices on PHP seven.ane (we already know information technology is deprecated, and already employ openssl if information technology is not installed)
one.2.34 – 08/Nov/2017
- TWEAK: Remove calls to the deprecated screen_icon() function
- TWEAK: Remove some unnecessary arranged translation files
- TWEAK: Add some translation files not previously included in the Premium version
- TWEAK: Update bundled Premium updater library to current (one.five.0)
one.ii.33 – 09/Oct/2017
- Gear up: The available/required settings for super-admins on multisite installs were non saving (Premium feature)
- Ready: When the admin fetched another user's current QR lawmaking, it embedded the wrong username (which was a cosmetic issue only – the code itself was right) (Premium feature)
1.ii.32 – 06/October/2017
- TWEAK: Update bundled updater in Premium to latest version (1.4.eight)
1.two.31 – 05/Oct/2017
- FEATURE: (Relevant to Premium version): Automatically generate new emergency codes when they run out, including upon view of settings if at that place are none (due eastward.g. on upgrade from complimentary to Premium)
- TWEAK: Lawmaking-styling consistency tweaks
1.two.30 – eighteen/Sep/2017
- Prepare: TML shortcode forms were non working properly for non-TFA users
1.2.29 – 16/Sep/2017
- Set up: Foreclose double-testify of TFA field on TML default login folio (regression)
- Ready: Restore functionality on TML shortcode forms (regression, probable due to changes in TML)
- TWEAK: Restore the spinner to proper size on all forms
- TWEAK: A few very pocket-sized-scale code fashion make clean-ups
ane.2.27 – 29/Aug/2017
- TWEAK: Add together the new 'PHP Requires' header to readme.txt
- TWEAK: Correct a couple of incorrect translation domain references
one.2.26 – 08/Aug/2017
- Ready: Do not asking TFA code on TML reset password course (regression, likely due to changes in TML)
- APOLOGIES: 1.2.25 was a faulty release that would block logins. You should immediately update.
one.2.24 – 05/Aug/2017
- TWEAK: Update to the latest version of the updater library (Premium)
ane.2.23 – 15/Jun/2017
- TWEAK: Let admins to reset users' individual keys (Premium)
i.two.22 – 23/May/2017
- TWEAK: Update updater library to electric current version (Premium)
- TWEAK: Apply college-quality spinner paradigm
- COMPATIBILITY: Marker every bit uniform with WP four.viii
one.ii.21 – 22/February/2017
- TWEAK: Update jquery-qrcode library to latest release (0.fourteen.0)
- TWEAK: Explicitly encode spaces in WordPress usernames (obviously resolves a problem with a detail iPhone app)
i.two.20 – 17/February/2017
- TWEAK: Work effectually a bug seen with strlen() on 1 particular PHP install
- FIX: The line purporting to carry witness the current UTC time was in fact taking your WordPress timezone into account. It has at present been adapted to show both to avert ambiguity.
- FIX: ane.ii.18 used a PHP five.4+ only role, whereas nosotros support PHP five.3+
1.ii.17 – 09/February/2017
- Prepare: Prepare back up for login widgets from Theme My Login
1.ii.xvi – xxx/Jan/2016
- Set: Fix result whereby if yous lot were already logged in and managed to visit a login form, you lot lot would non be asked for a TFA code
1.ii.fifteen – 23/Jan/2017
- FEATURE: Add together dorsum up for login widgets from Theme My Login
- UPDATER: (Premium version): update to the latest updater form, including the new ability to automatically update
1.two.fourteen – 02/Jan/2017
- TWEAK: Add missing internationalisation headers to the main plugin file
1.2.thirteen – 31/Aug/2016
- TWEAK: Internationalisation implementation was not previously compatible with wordpress.org's translation organisation
1.ii.12 – xx/May/2016
- Feature: Compatibility with https://wordpress.org/plugins/use-ambassador-password/ – when TFA is enabled on an account, the TFA credentials of the user whose countersign was supplied are allowed (and required)
1.ii.11 – eighteen/May/2016
- TWEAK: Update bundled select2 to version iv.0.ii
- Gear up: If the [twofactor_user_qrcode] shortcode (Premium version) was used without other short-codes, so the lawmaking would not display
i.ii.x – 31/Mar/2016
- TWEAK: Prefer openssl, if nowadays, to the deprecated mcrypt. Annotation that if yous migrate a site from a server without openssl to a server without mcrypt, then because of mcrypt's non-compliant padding, y'all volition demand to either install php-mcrypt on the new server, or disable TFA (via define('TWO_FACTOR_DISABLE', true); in your wp-config.php) to allow users to be able to log in. This also applies if the source site did accept openssl, merely for users who hadn't logged in since installing this update.
- TWEAK: Make the $simba_two_factor_authentication_premium object globally bachelor
- COMPATIBILITY: Mark equally tested on WP four.5
1.ii.8 – 12/December/2015
- Feature: Add back up for the Affiliates-WP login form
- TWEAK: Defeat WooCommerce loading an onetime version of the select2 script onto the TFA settings page, and breaking the user selector (should work this time)
1.2.half-dozen – 11/Nov/2015
- TWEAK: Defeat WooCommerce loading an one-fourth dimension version of the select2 script onto the TFA settings folio, and breaking the user selector
- TWEAK: Tested on WordPress iv.4
- TWEAK: Utilise h1 for heading style on admin folio, not h2
- Gear up: The "You lot'll need to utilize TFA to login in hereafter" link for users for whom TFA is compulsory (Premium) was to the wrong folio
one.2.4 – 09/November/2015
- TWEAK: Make window settings filterable
i.2.iii – 19/October/2015
- Fix: Set upwardly bug in i.ii.2 that could lock out users without TFA settings
i.ii.ii – 16/October/2015
- TWEAK: Brandish dashboard observe if TWO_FACTOR_DISABLE is defined in wp-config.php, to forbid time wasted wondering why nothing is happening
i.two.ane – 08/Oct/2015
- Characteristic: (Premium version) – Require users (of configured roles) to use TFA (optionally after a configurable amount of fourth dimension)
one.i.21 – 25/Aug/2015
- TRANSLATIONS: Translation files can now be used (translators welcome!)
- TRANSLATION: Swedish translation added, courtesy of Bo Sving
1.one.19 – 20/Aug/2015
- TWEAK: Remove a pointless nonce cheque
one.ane.xviii – 01/Aug/2015
- COMPATIBILITY: Tested with WP four.3 (RC1) and WooCommerce 2.4 (RC1) – no problems constitute (i.due east. previous releases believed to exist already uniform)
- Set: When the admin is showing codes for other users, QR codes were not displaying correctly since 1.1.13
1.ane.17 – 22/May/2015
- TWEAK: Introduce convenience method for developers wanting to verify that TFA is active (Premium)
- Gear up: Set functioning of [twofactor_conditional] shortcode (Premium)
- Ready: Set fatal fault introduced in convenience method in 1.i.xvi
ane.ane.15 – thirteen/May/2015
- Fix: Fix conflict with 'reset countersign' form with "Theme My Login" plugin
1.1.14 – 12/May/2015
- Prepare: Add TFA support to the WooCommerce login-on-checkout course (previously, TFA-enabled users could not log in using it)
i.i.13 – eleven/May/2015
- TWEAK: Use jquery-qrcode to generate QR codes, replacing external dependency on Google
- TWEAK: Update arranged select2 library to iv.0.0 release (was rc2)
one.1.12 – 22/April/2015
- FIX: Fix corner-case where the user's login looked like an email address, but wasn't the business relationship address. In this instance, a OTP countersign was e'er requested.
- Ready: When the username does non exist, front-stop should non request TFA code.
one.one.11 – 21/Apr/2015
- TWEAK: Forestall PHP notice if combining with bbPress
- TWEAK: Added more panel logging if TFA AJAX asking fails
- TWEAK: Add together some measures to overcome extraneous PHP output breaking the AJAX conversation (eastward.g. when using strict debugging)
1.one.10 – twenty/Apr/2015
- SECURITY: Fix possible not-persistent XSS upshot in admin expanse (https://blog.sucuri.net/2015/04/security-informational-xss-vulnerability-affecting-multiple-wordpress-plugins.html)
- FIX: Don't go involved on "lost password" forms (intermittent issue with "Theme My Login")
ane.i.9 – xv/April/2015
- TESTING: Tested with "Theme My Login" – https://wordpress.org/plugins/theme-my-login/ – no issues
- TWEAK: Practice a little fleck of status logging to the browser'south developer console on login forms, to assist debugging any issues
- TWEAK: Add a spinner on login forms whilst TFA status is being checked (WP three.viii+)
- TWEAK: Make sure that scripts are versionned, to forestall updates non existence immediately constructive
- TWEAK: Make sure OTP field on WooCommerce login class receives focus automatically
1.i.viii – 14/Apr/2015
- FIX: Gear up an issue on sites that forced SSL admission to admin surface area, simply not to front end finish-stop, whereby AJAX functions could fail (east.yard. showing latest lawmaking)
- FIX: Version number was non shown correctly in admin screen since ane.1.v
- TWEAK: Testify proper plugin URI
i.ane.7 – ten/Apr/2015
- Set: Set up plugin compatibility with PHP five.six
- Set: TFA was ever made agile on XMLRPC, even when the user turned it off
1.one.half-dozen – 09/Apr/2015
- TWEAK: Change various wordings to make things clearer for new-comers to two-factor authentication.
ane.i.5 – 07/April/2015
- FEATURE: Admin users (Premium version) can show codes belonging to other users, and activate or de-activate TFA for other users.
- PREMIUM: Premium version has now been released: https://www.simbahosting.co.uk/s3/production/two-factor-hallmark/. Features emergency codes, personal support, and more than short-codes allowing y'all to custom-design your own forepart-stop folio for users.
- TWEAK: Premium version now contains support link to the proper identify (not to wordpress.org's free forum)
- TWEAK: Added a constant, TWO_FACTOR_DISABLE. Ascertain this in your wp-config.php to disable all TFA requirements.
- Ready: Prepare a bug introduced in version one.i.ii that could prevent logins on SSL-enabled sites on the WooCommerce class when non accessed over SSL
i.1.three – 04/April/2015
- TWEAK: Provide "Settings saved" notice when user's settings are saved in the admin area (otherwise the user may exist wondering).
1.1.ii – 03/Apr/2015
- FIX: Include blockUI JavaScript (the lack of which acquired front end-end options non to save if you lot did not have WooCommerce or another plugin that already used blockUI installed)
- Characteristic: Don't show anything on the WooCommerce login grade unless user is using 2FA (i.e. conduct like WP login class)
- Characteristic: Added ix new shortcodes for custom-designed front end-terminate screens (Premium – forthcoming)
i.1.1 – 30/Mar/2015
- Support added for multisite installs. (Plugin should exist network-activated).
- Support added for super-admin role (information technology'southward not a normal WP office internally, so needs custom handling)
- Tested + compatible on upcoming WP 4.two (tested on Beta 3)
- Re-add choice to crave 2FA over XMLRPC (without specific lawmaking, XMLRPC clients don't/tin can't utilise 2FA – simply requiring information technology effectively blocks hackers who want to crevice your password past using this weakness in XMLRPC)
1.0 – 20/Mar/2015
- Start version, forked from Oskar Hane'due south https://wordpress.org/plugins/two-factor-auth/
- Support for email "two-factor" removed (email isn't really a second cistron, unless yous lot have multiple electronic mail accounts and guard where your "lost login" emails get to)
- WooCommerce support added to the principal plugin. Load WooCommerce JavaScript merely on pages where it is needed.
- Utilise AJAX to refresh current code (rather than reloading the whole page)
- Added WordPress nonces and user permission checks in relevant places
- Shortcode twofactor_user_settings added, for forepart-cease settings
- User interface simplified/de-cluttered
Source: https://sanderssucken.blogspot.com/2022/04/authentication-failed-please-try-again.html
0 Response to "Stackoverflowoops There Has Been an Error Please Try Again Later"
Post a Comment